Web: Cybersecurity Frameworks
Web: Cybersecurity Frameworks
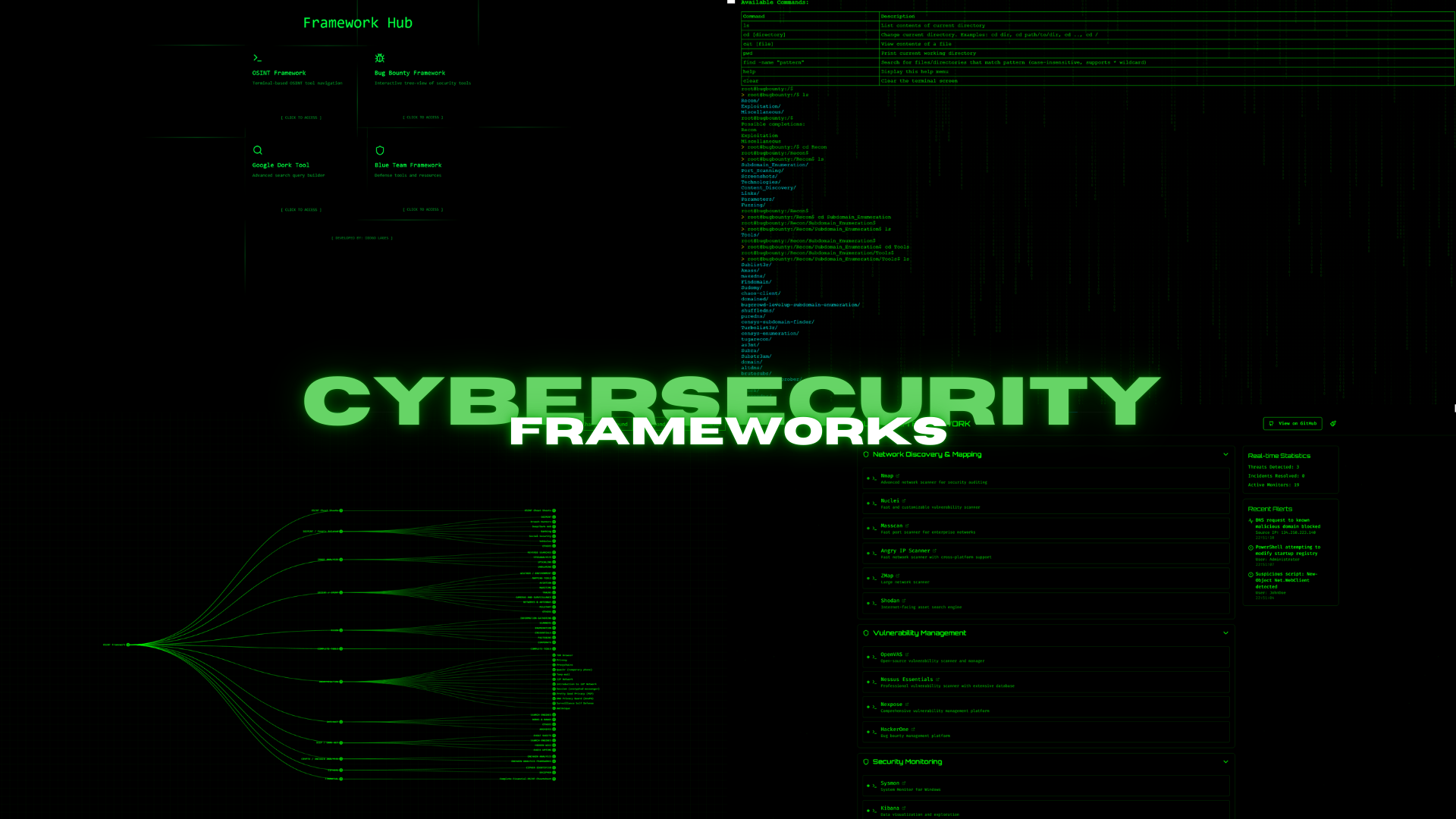
The frameworks presented here include Framework Hub (The Main Dashboard), OSINT Framework , Blue Team Framework , and Bug Bounty Framework . These frameworks are designed to help users find tools specific to each area, such as Blue Team, Bug Bounty, and OSINT.
Cybersecurity Frameworks Repositorys
- Link: Framework Hub Repository
- Link: OSINT Framework Repository
- Link: Blue Team Framework Repository
- Link: Bug Bounty Framework Repository
Overview of the Projects
Shared Technologies
Most of these projects leverage modern web development tools:
- React: For building dynamic and interactive user interfaces.
- TypeScript: To ensure type safety and improve maintainability.
- Vite: For fast development and build processes.
- CSS/Styled Components: For consistent and visually appealing designs.
The Bug Bounty Framework stands out as it uses pure HTML and JavaScript, providing a lightweight terminal-based experience.
Features Across Projects
Framework Hub
- A centralized dashboard offering access to multiple frameworks, including OSINT, Bug Bounty, Blue Team, and Google Dork tools.
- Modular design allows users to switch between frameworks seamlessly.
OSINT Framework
- Unified search interface across multiple OSINT sources.
- Categorized resources presented in a tree view for easy navigation.
Blue Team Framework
- Organized security tools grouped by categories like Network Discovery, Vulnerability Management, and Threat Intelligence.
- Simulated security alerts and a cyberpunk-themed UI for an immersive experience.
Bug Bounty Framework
- Terminal-like environment with file system navigation and search functionality.
- Dynamic animations like binary rain, Matrix effects, and cyber grids for an engaging experience.
Interface
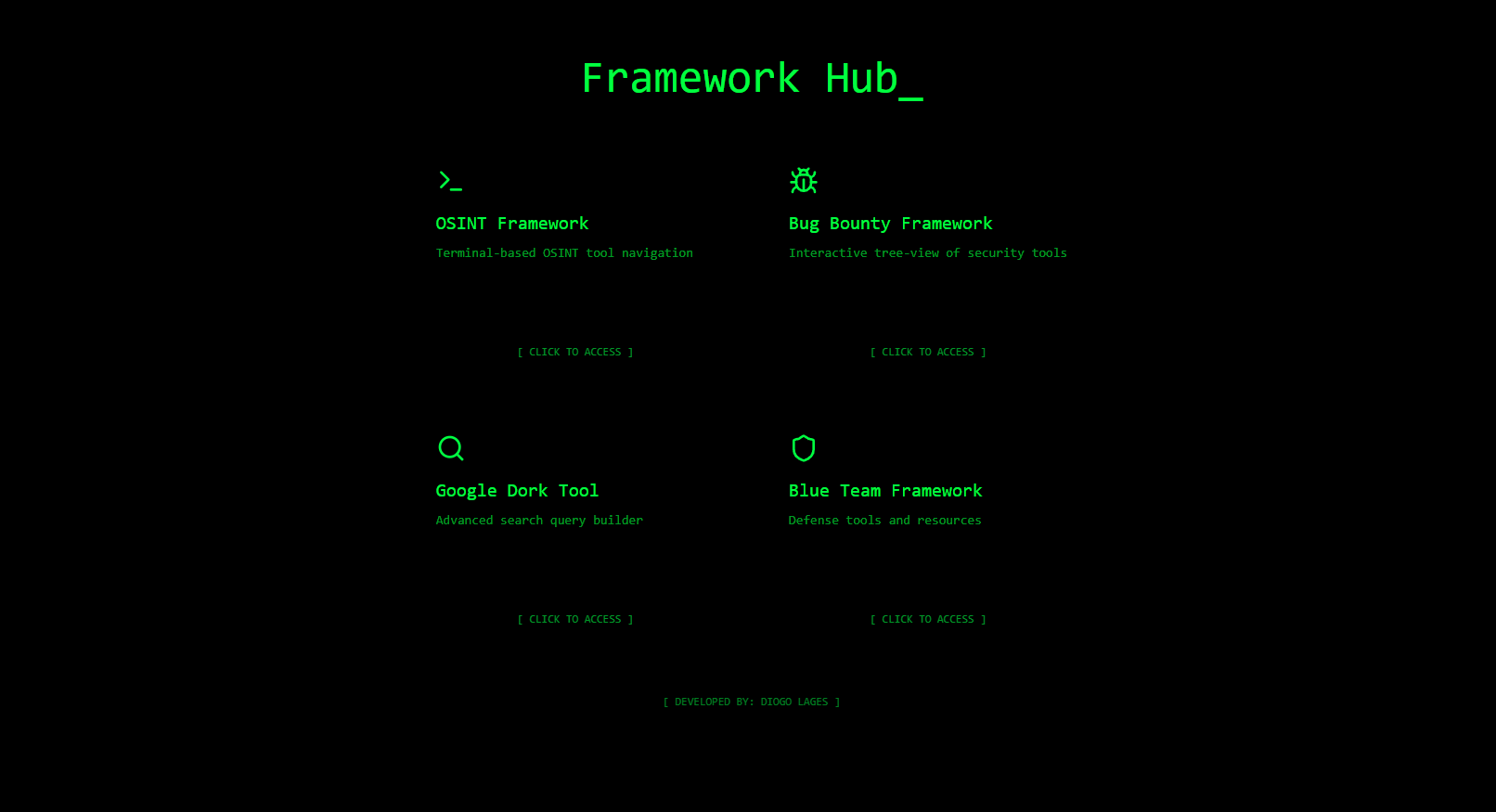
Framework Hub: Centralized access to all frameworks.

OSINT Framework: Tree view search and categorized resources.
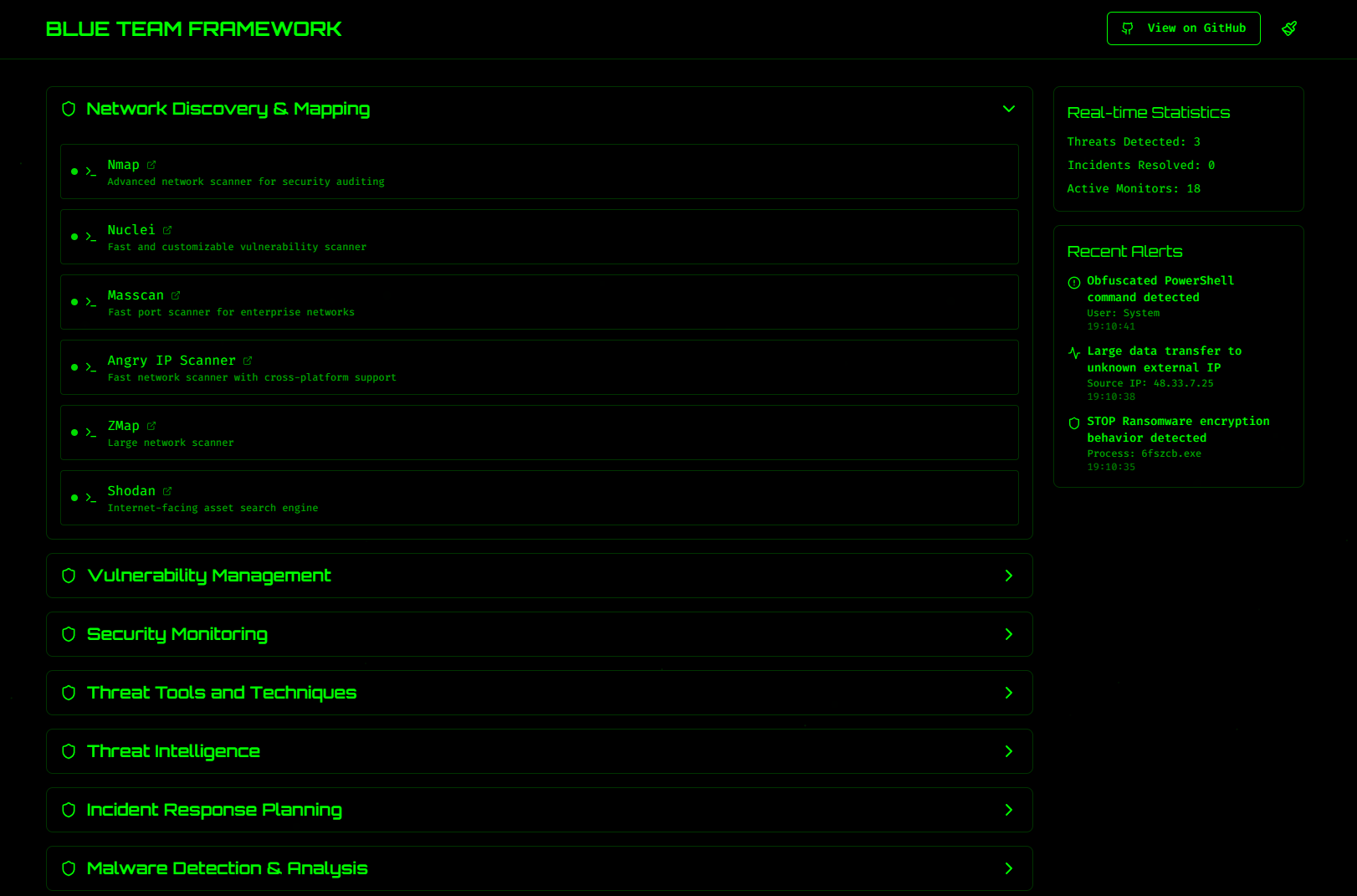
Blue Team Framework: Cyberpunk-themed UI with simulated alerts.

Bug Bounty Framework: Terminal-like environment with animations.
Ethical Considerations
Each project is designed with ethical use in mind:
- Respect Privacy: Always ensure compliance with privacy laws and regulations.
- Legal Compliance: Adhere to all applicable laws when conducting security research or bug hunting.
- Responsible Disclosure: If vulnerabilities are discovered, follow responsible disclosure practices.
- Defensive Use Only: Tools like the Blue Team Framework are for defense, not for unauthorized or malicious activities.
This post is licensed under CC BY 4.0 by the author.