Bug Bounty Tools Assistant
A Python-based interactive CLI tool designed to assist bug bounty hunters and security testers by providing quick access to commands for Recon, Exploitation, and Miscellaneous tasks.
Bug Bounty Tools Assistant Repository
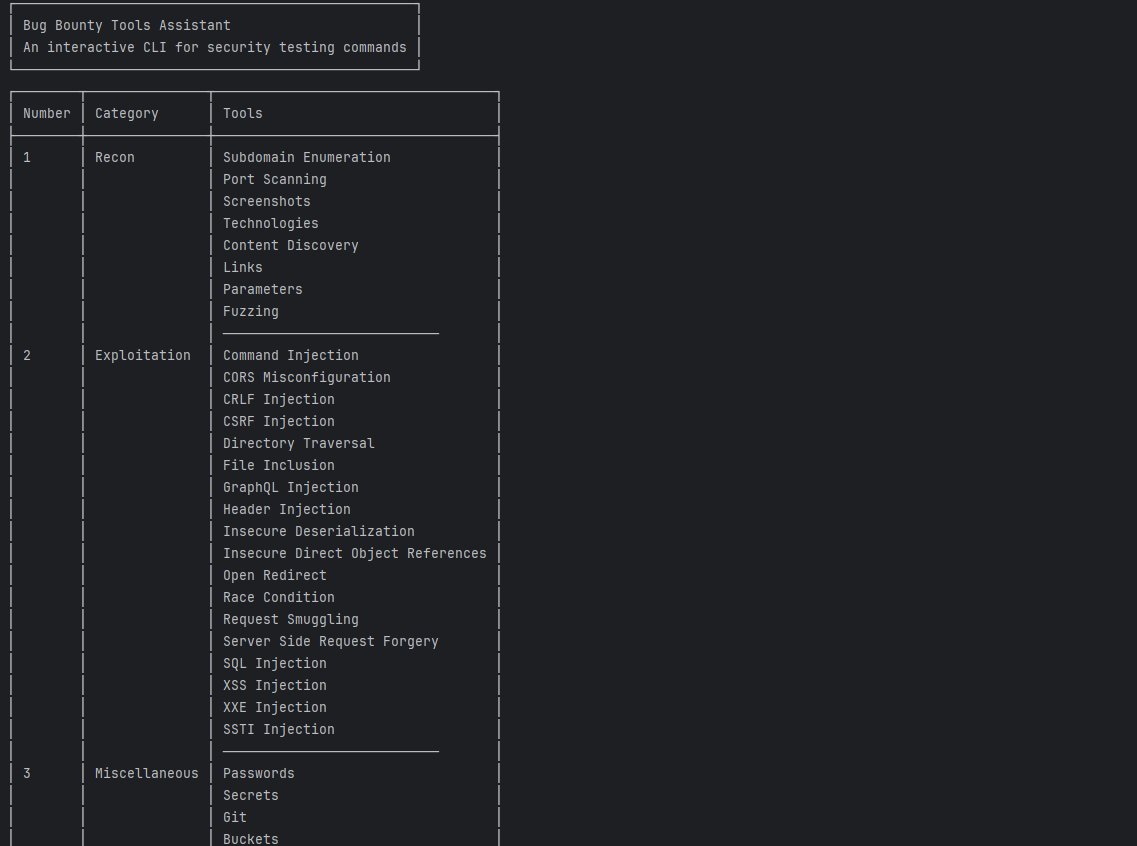
Features
- Interactive Menu: Navigate through categories like Recon, Exploitation, and Miscellaneous with ease.
- Command Execution: Execute or simulate commands for tools like
commix,nuclei,ffuf, and more. - Clipboard Support: Commands are copied to your clipboard for quick use.
- Extensible: Easily add new tools or categories by modifying the code structure.
- Rich Output: Clear and visually appealing output using the
richlibrary.
How It Works
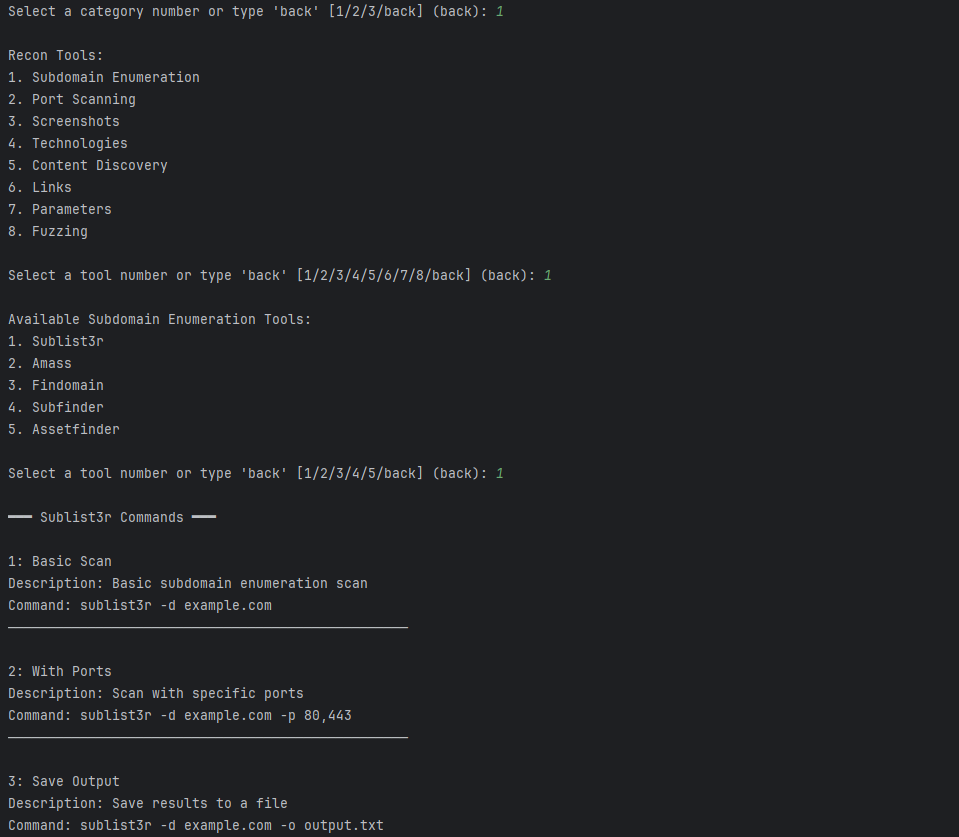
The Bug Bounty Tools Assistant is an interactive CLI tool that allows users to select from predefined categories (Recon, Exploitation, Miscellaneous) and tools within those categories. Once a tool is selected, the associated command is displayed, copied to the clipboard, and optionally executed. The tool supports both real execution and simulated execution for testing purposes.
For example:
- Run the program using
python main.py. - Select a category (e.g., Recon).
- Choose a tool (e.g., Subdomain Enumeration).
- The tool’s command will be displayed, copied to your clipboard, and optionally executed.
Code Structure
- main.py: Entry point of the application. Displays the main menu and handles user interaction.
- utils/menu.py: Contains functions for displaying the main menu and handling tool selection.
- tools/: Directory containing modules for different categories (
recon.py,exploitation.py,miscellaneous.py). - execute_command.py: Handles the execution or simulation of commands.
- LICENSE: License file for the project.
Interface
Future Enhancements
- Add support for additional tools and categories.
- Introduce a web-based GUI for easier accessibility.
- Implement automated updates for tool commands and configurations.
- Add integration with APIs for real-time vulnerability scanning.
Ethical Considerations
This tool is intended for educational and ethical purposes only. Users are responsible for ensuring they have proper authorization before using this tool on any system or network. Unauthorized use of this tool may violate laws and regulations. Always follow ethical guidelines and respect privacy when conducting security tests.